SUCCESS STORIES
CarDealster
App Available for iOS Users Only
The Client
CarDealster is an iPhone app designed for automobile salespeople, small dealerships, and vehicle brokers. The app is revolutionizing the automotive sales landscape in U.S. by empowering users to stay connected with their iPhone contacts, effortlessly generating 5-star reviews, sharing service coupons, and accessing critical vehicle information, including VIN decoding and NHTSA Recall Data – all conveniently from their iPhones.
App Gallery


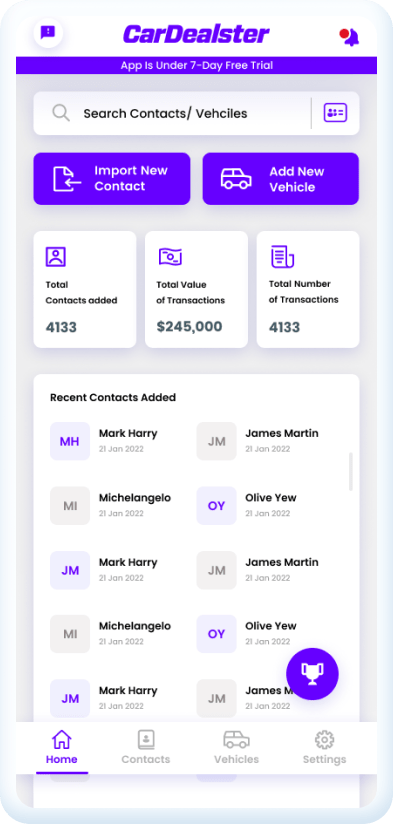
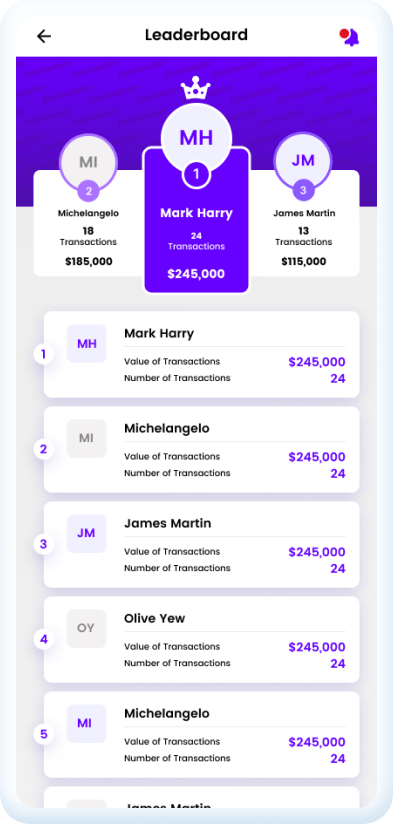

At a glance
Services:
- iOS app Development
- CMS Portal Development
- Quality Assurance
Techstack:
- Swift (For iOS)
- Plumber (UI Kit)
Challenge
Developing CarDealster app presented a significant challenge, primarily centered around creating a seamless process for users to capture car chassis numbers through the app’s camera and instantly access a third-party database for comprehensive car information retrieval. The objective was to eliminate manual data entry and enhance user convenience. However, achieving this setup involved addressing several hurdles.
The foremost challenge involved ensuring the accuracy and reliability of data retrieved from the third-party database. Data validation mechanisms needed to be implemented to maintain the app’s credibility. Additionally, privacy and security of the data were also a paramount concern for our client.
Solution
To overcome these challenges, our expert developers devised ingenious solutions. Leveraging Apple’s Vision Kit and AV Kit, they enabled the app to read the car’s chassis number via number read or barcode using the device’s camera, offering users the flexibility to enter it manually as well. This breakthrough allowed seamless access to the entire record and data of the car, retrieved based on the chassis number.
To ensure data reliability and accuracy, Veroke’s experts implemented rigorous validation and verification mechanisms. Comprehensive testing was conducted to validate the data retrieved from the third-party database, guaranteeing users access to trustworthy information. Furthermore, robust authentication protocols were also put in place to protect the user data.